Viettel Cyber Security (VCS) announced its role in the discovery and responsible disclosure of critical zero-day vulnerabilities in Microsoft SharePoint, which are now confirmed to be actively exploited in real-world attacks. These vulnerabilities pose a significant risk to organizations globally that rely on on-premises SharePoint servers for document storage and collaboration.
The vulnerability chain, originally identified by VCS, allows threat actors to bypass authentication, upload webshells, and remotely execute malicious code without prior access. A particularly critical aspect is the potential for attackers to extract ValidationKey and DecryptionKey, enabling persistent control over affected systems even after security patches are applied. SharePoint Online in Microsoft 365 is not affected by these vulnerabilities.
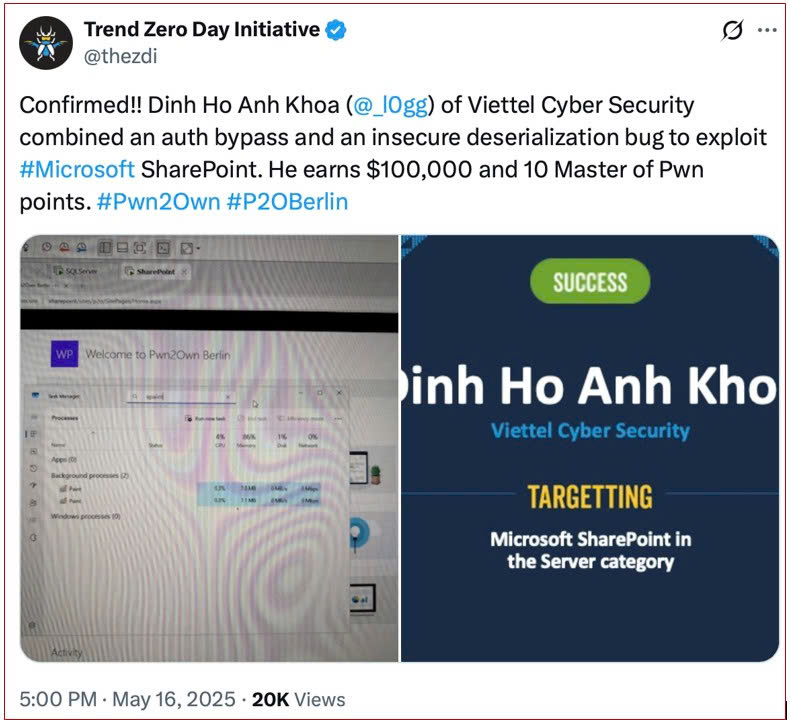
The journey to uncovering these vulnerabilities began on May 16, 2025, at Pwn2Own Berlin 2025, where Dinh Ho Anh Khoa, a member of VCS’s elite research team, successfully chained an authentication bypass with an insecure deserialization bug to gain unauthorized access in SharePoint. This exploit earned him $100,000 and was subsequently assigned CVE-2025-49704 and CVE-2025-49706.
VCS immediately reported these findings to Microsoft and Trend Micro’s Zero Day Initiative (ZDI), the Pwn2Own organizer, through responsible disclosure programs, aligning with global security standards.
On July 8, 2025, Microsoft released patches for CVE-2025-49704 and CVE-2025-49706 as part of its July 2025 Patch Tuesday security update. Following this, Viettel Cyber Security Threat Intelligence issued an early warning and guidance to its customers to mitigate potential exposure.
However, on July 19, 2025, Microsoft confirmed active attacks targeting on-premises SharePoint Server customers, exploiting vulnerabilities partially addressed by the July Security Update. These new exploits were later named CVE-2025-53770 and CVE-2025-53771. Microsoft subsequently released additional security updates designed to fully protect customers using all supported versions of SharePoint affected by these newly identified CVEs.
Following Microsoft’s official disclosure, VCS has confirmed that these vulnerabilities are now being actively exploited at scale, primarily on servers that have not yet applied Microsoft’s latest patches. Immediate action is strongly recommended to prevent potential compromise and protect critical infrastructure.
This is not the first time VCS has reported critical vulnerabilities to major global technology companies. Over the years, VCS has responsibly disclosed numerous high-impact security flaws in products from Microsoft, Oracle, HP, Canon, Synology, QNAP Systems, and Nvidia, helping these companies patch issues before they could be weaponized by malicious actors.
“At Viettel Cyber Security, our top priority is clear: to defend the ecosystem against real-world threats,” said a VCS spokesperson. “By sharing what we know, we aim to strengthen the entire security community and help organizations understand these vulnerabilities and take decisive action to stop attackers.”
Recommended Actions for Organizations
Viettel Cyber Security has released detailed technical analysis and guidelines to protect against CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771, including prevention strategies, detection patterns, and threat hunting techniques. Organizations are strongly advised to take the following immediate actions to mitigate risks from this vulnerability chain:
For Supported SharePoint Versions (SharePoint Server 2016, 2019, and Subscription Edition):
- Immediately apply the July 2025 Security Update from Microsoft, which patches CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771.
- Rotate machine keys, then restart IIS.
- Enable Antimalware Scan Interface (AMSI) on all SharePoint servers.
- Restrict direct internet access from SharePoint servers to limit data exfiltration or malware downloads.
- Use a Web Application Firewall (WAF) or reverse proxy to proactively filter out malicious requests.
For End-of-Life SharePoint Versions (No Security Patches Available – SharePoint 2010, 2013):
- Plan to upgrade to supported versions to receive security updates.
- Temporarily implement compensating technical controls by configuring a firewall, WAF, or reverse proxy rules to block all requests to
/ToolPane.aspx, including requests with appended pathInfo. - Inspect and block suspicious POST requests.
- Monitor logs and file changes in the
/LAYOUTS/directory. - Isolate legacy SharePoint servers from the internet if they are used solely for internal operations.
- Strengthen detection using EDR or antivirus solutions.